Is Google Wallet Safe?
We have recently covered a possible link between the delayed release of the Samsung Galaxy Nexus and NFC issues between Google and Verizon related to security and general competition.

And we have discussed the Google Wallet NFC technology way back when we started in June this year, so here is an update on the Google Wallet security issue.
Thanks to a recent research paper from Viaforensics, we can report that recent research seems to suggest that despite everyone’s hatred of Verizon for delaying the US release of the Samsung Galaxy Nexus, they may have had their reasons and perhaps Google may need to buck their ideas up when it comes to the security of their new NFC mobile payment technology.
Google do not have the best track record for security in their App marketplace:
This comes after many issues that relate to security and Malware found on apps in their own Android marketplace.
So, should Google be trusted with more of our credit card details? Or should they just stick to providing information for free and making shed loads from adverts and stop selling actual products and services?…of course this is a joke.
Google Wallet does not encrypt credit card details safely:
So what could be the problem with Google Wallet?
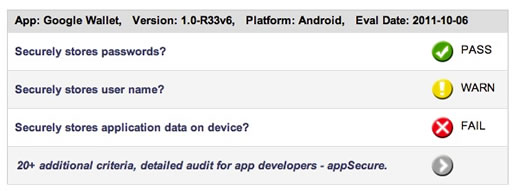
*Note that these tests were done on a “rooted” device.
The report suggests that Google Wallet does a really good job in storing passwords safely, but with no encryption on the credit card number, balance and other info, the report does hint that things could be improved here.
However on top of this, the additional findings by ViaForensics in a report titled “Forensic security analysis of Google Wallet” suggests that further data stored in the SQLite databases in an unencrypted way includes:
[arrowlist]
- Name on the card
- Card limit
- Expiration date
- Transaction dates and location
- The last four digits of your card
[/arrowlist]
Oh yes, that just about covers it.
And so it seems, like pretty much everything that you need to steal a persons details, in order to do fraudulent purchases will be available in this database, unencrypted, to be used with “relative” ease.
The testing on a rooted phone did mean that the researcher had root or privileged control of the phone. And the actual credit card number was not accessible at this level as it is stored in the NXP chip.
*I must stress I am not a mobile security expert but do want to point out that there are differences between a rooted device and a non rooted device with increased difficulties associated with the non rooted device which was not the subject of these tests.
Image of credit card recoverable from cache:
The research method uncovered an option to create a recoverable PNG image of the credit card which had some of the details from the researchers card within the image and could have been used, according to the report, for social engineering attacks.
Most of the files were pictures of blank cards however one of the cards had been updated to reflect some of my credit card information. While this was an initial and small finding, before I could complete this article Google pushed out an update to Google Wallet and the card image no longer contained the data. While very little data was exposed, the most problematic was the card expiration date which is a key piece information needed for Card Not Present (“CNP”) transactions.
In summary the researcher concluded by saying:
While Google Wallet does a decent job securing your full credit cards numbers (it is not insecurely stored and a PIN is needed to access the cards to authorize payments), the amount of data that Google Wallet stores unencrypted on the device is significant (pretty much everything except the first 12 digits of your credit card).
Scary stuff, or a report based on unlikely events?
Anthony Munns